HTB Arkham writeup-Java Encrypted Deserialization attack(English)
Summary
This host is relatively hard to get the initial foothold; relatively easy to do privilege escalation. That said, I needed to roll up my sleeve to fully understand how's everything working for getting Alfred's shell. Couldn't believe this is a "medium" level machine.
I believe any automated scanners cannot find the injection point because we need the encryption/ decryption key in the first place (not sure if brute force attack is a reasonable option here). Yes, the chain of human mistakes made everything possible.
Useful documents
Other than 8, no documents mention how to inject encrypted malicious object. That is a part of the reason I'm writing this post. I think I have to give back something valuable to the community!
- https://medium.com/abn-amro-red-team/java-deserialization-from-discovery-to-reverse-shell-on-limited-environments-2e7b4e14fbef
- https://securitycafe.ro/2017/11/03/tricking-java-serialization-for-a-treat/
- https://www.n00py.io/2017/11/exploiting-blind-java-deserialization-with-burp-and-ysoserial/
- https://stackoverflow.com/questions/22814/how-to-decode-viewstate
- https://www.synacktiv.com/ressources/JSF_ViewState_InYourFace.pdf
- https://www.alphabot.com/security/blog/2017/java/Misconfigured-JSF-ViewStates-can-lead-to-severe-RCE-vulnerabilities.html?source=post_page---------------------------
- https://medium.com/@D0rkerDevil/how-i-found-a-1500-worth-deserialization-vulnerability-9ce753416e0a
- https://gist.github.com/cdowns71/76d99ad0829ceef3a83761dbeee3b66d
- https://www.exploit-db.com/docs/english/44756-deserialization-vulnerability.pdf
- https://github.com/joaomatosf/jexboss
Attack tree-ish mind map

Port scan

First impression
SMB --> unusual open port (8080: HTTP) might be the way.
SMB
enum4linux. Oh well...

smbclient

Found something, but encrypted.

Personally, I always try to avoid bruteforcing. No harm to give it a shot with "foremost" (forensic tool).

http://foremost.sourceforge.net/
Originally developed by the United States Air Force Office of Special Investigations and The Center for Information Systems Security Studies and Research , foremost has been opened to the general public.

"bak" is usual suspects.

Yeah, I found a key... for what? Hmm, the key for this? Anyway, let's check 8080 out.
8080
The application seemed to be under development. Only the subscription function worked.


the official document says as follows:
- Base64 is used for all encoding and decoding.
- DES is the default encryption algorithm
- ECB is the default mode
- PKCS5Padding is the default padding
- HmacSHA1 is the default MAC algorithm
So this looks very easy (quickly came up with a few lines of Python codes), but I couldn't get the big picture at this point. Let's try to understand the object.
Knowing the object
original object
wHo0wmLu5ceItIi%2BI7XkEi1GAb4h12WZ894pA%2BZ4OH7bco2jXEy...
Percent encoded. This has nothing to do with deserialization per se. URL decode. Referring to the document, we need to base 64 decode.
Àz4ÂbîåÇ´¾#µä-F¾!×eóÞ)æx8~Ûr£\LµE)VUVÇðÔïBÙà9´ÜÀö¡ãaêñ£HÖï;µ:Jz¥Rg¸\ëLYXRñMb
DES encrypted? Yes. ah, where to put HMAC? Do we have to take PKCS5Padding into consideration?

While I've been struggling, I found someone's memo about how to exploit this object (please refer to 8 in the above). I finally understood where the HMAC should be added. Tried code injection (ping back to my Kali) and confirmed that worked.
If you're a member of HTB VIP and never tried this machine, get your hands dirty now, I insist!
FUD
I tried a few obfuscation tools (like TheFatRat) but all was detected. Not sure what kind of EDR sat there at that time (Windows Defender, actually). The only exception was nc64.exe (Now I'm thinking "Invoke-PowerShellIcmp"(nishang) might work. I don't have a chance to check that out yet though).


Internal Enumeration
"whoami" ; Alfred (the author might be a big fan of Batman). I found a zip file on "Downloads" directory. OST file with an attachment below.

UAC bypass
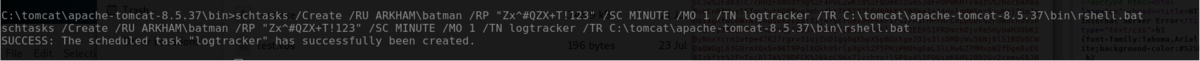
As far as I know, the most painless way to get the shell is schtasks. Check out other writeups how everyone over-complicates the problem.
Someone might say this is not the pure "bypass". Yeah that might be right. Haha, I'm just lazy.